News Corp Data Breach : State-Sponsored Attackers Had Access to Network for Two Years
Last year, News Corp disclosed a data breach that it said had been carried out by state-sponsored attackers. However, in a recent letter to employees, News Corp revealed that the attackers had actually been on their network for nearly two years by the
Reducing Dwell Time: Crucial Steps for Effective Cybersecurity
In the world of cybersecurity, the term “dwell time” refers to the length of time that an attacker remains undetected within a network. The longer an attacker is able to dwell within a network, the more time they have to carry out their
Protect Your Computer from Sneaky Hacks with These 5 Powerful Tips Against Rubber Ducky Cables
What is this? Rubber ducky cables are USB devices designed to look like normal charging cables or other types of USB devices. In this blog, we will discuss the basics of rubber ducky cables, their applications, and how they can pose a threat
Why Phishing Filters Fail and Phishing Simulation Can Help
Phishing is a widespread and constantly evolving threat affecting individuals and organizations. It is a type of cyber attack that involves criminals posing as trusted entities in order to trick people into revealing sensitive information, such as passwords and financial information. Despite the
The Accountant’s Tale: A Cautionary Story of a Phishing Attack and Incident Response
Introduction Jack was a highly competent accountant working for a small financial firm. He had been with the company for several years and was well-respected by his colleagues and superiors. One day, Jack received an email that looked like it was from one
The Rise of Finworth: A Fictional Tale of Ethics and Security in the Finance Industry
Disclaimer: The names of the companies mentioned in this story are fictional and any resemblance to real companies is purely coincidental. The purpose of this story is to illustrate the importance of ethics and security in the finance industry and is not intended
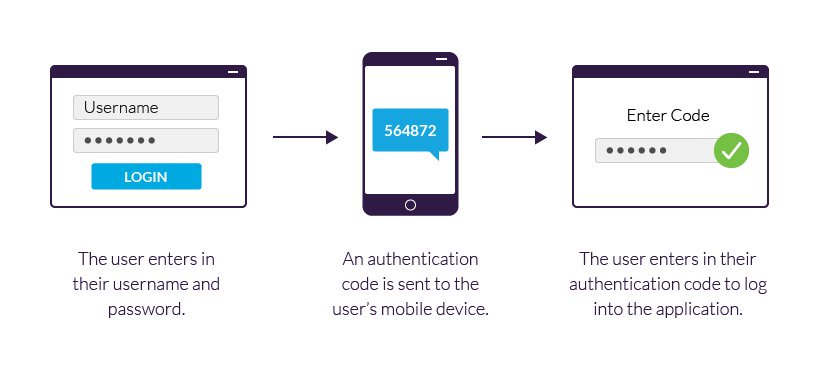
Two-Factor Authentication: Types, Benefits, and How to Choose the Right One for You
Introduction: Two-factor authentication (2FA) is a security process that requires users to provide two separate forms of identification in order to access their accounts. It adds an extra layer of protection beyond a password, ensuring that even if a password is compromised, the

Recent Comments