
What is Digital Forensics? How to recover lost data
Introduction to Digital Forensics

In our increasingly digital world, data is one of our most valuable assets. Whether it’s personal photos, important business documents, or sensitive financial information, losing it can have serious consequences. Fortunately, digital forensics plays a vital role in both understanding the causes of data loss and recovering lost data. Let’s explore how this discipline can safeguard your data and help you recover what may seem irretrievably lost.
Understanding Digital Forensics
Definition and Scope of Digital Forensics
Digital forensics refers to the practice of investigating and analyzing data from digital devices, such as computers, smartphones, or servers, to uncover evidence of cybercrimes or data breaches. This process is critical in ensuring that data remains intact and can be used in investigations, whether it’s for solving a cybercrime or retrieving lost files.
Importance of Digital Forensics in Today’s Digital Age
As cyber threats continue to rise, digital forensics has become essential for identifying, mitigating, and preventing security breaches. It not only helps uncover cybercriminals but also provides a way to understand the cause of data loss and the scope of damage, ensuring organizations can protect sensitive information and meet regulatory requirements.

Key Areas of Application
- Cybercrime: Digital forensics tracks hackers, identifies attack methods, and gathers evidence to prosecute offenders.
- Fraud Investigation: Forensics help in identifying fraudulent activities by analyzing digital trails left behind.
- Corporate Security: It enables businesses to respond to and prevent future cyberattacks by investigating internal data breaches or compromised systems.
Branches of Digital Forensics
Digital forensics is a broad field with specialized branches, each focusing on a different type of data, device, or area of investigation. These branches include:
1. Computer Forensics
Computer forensics focuses on the recovery, investigation, and analysis of data stored on computer systems, including desktops, laptops, and servers. It is used to uncover evidence of crimes such as hacking, fraud, or intellectual property theft. Investigators work with hard drives, file systems, and storage devices to recover deleted files and analyze activity logs.
2. Network Forensics
Network forensics involves the monitoring and analysis of network traffic to uncover cybercrimes, unauthorized access, and data breaches. By examining network logs, packet data, and communication patterns, investigators can trace the origin of cyberattacks and analyze how a system was breached.
3. Mobile Device Forensics
As smartphones and tablets store a significant amount of personal and business data, mobile device forensics focuses on retrieving data from these devices. Investigators recover call logs, text messages, app data, and even deleted information to trace the activities of users, particularly in criminal investigations.
4. Database Forensics
Database forensics is the branch dedicated to analyzing database management systems for evidence of cybercrime or unauthorized access. This includes investigating SQL injection attacks, uncovering unauthorized modifications, and recovering deleted records from databases.
5. Cloud Forensics
With an increasing amount of data being stored in cloud environments, cloud forensics focuses on the investigation of data hosted on cloud platforms. It involves the recovery of data from cloud services and tracking user activities, ensuring that information in cloud-based systems is secure and intact during investigations.
6. Memory Forensics
Memory forensics deals with the analysis of volatile memory (RAM) to uncover evidence. This branch is critical in investigating incidents like malware attacks, rootkit infections, and other malicious activities. Memory forensics tools can extract running processes, open files, and network connections, which can be pivotal in solving cybercrimes.
7. Forensic Data Analytics
Forensic data analytics applies analytical techniques to digital evidence to detect patterns or inconsistencies that might suggest fraudulent activities. This branch uses advanced data mining, statistical analysis, and machine learning methods to investigate large datasets and identify anomalies in financial transactions, for example.
8. Automotive Forensics
Automotive forensics is a niche but growing field that focuses on retrieving data from in-car systems such as infotainment systems, GPS devices, and event data recorders (EDRs). It can be critical in accident investigations, insurance fraud cases, or criminal investigations where vehicle data might provide crucial evidence.
Principles and Process of Digital Forensics
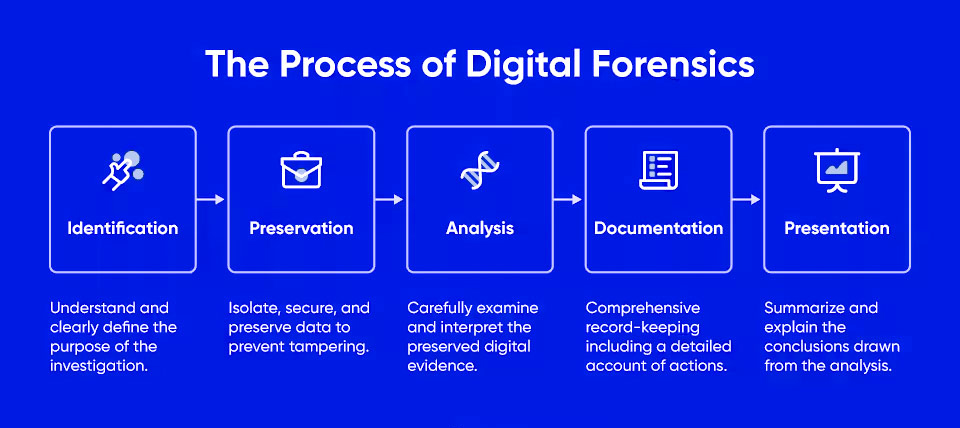
Core Principles: Preservation, Analysis, and Documentation
Digital forensics relies on a set of key principles that ensure the integrity of the evidence. The core principles include:
- Preservation: Ensuring that evidence is collected without altering or damaging it.
- Analysis: Reviewing data to identify patterns or malicious activity.
- Documentation: Keeping detailed records of the process and findings for legal use.
Steps in Digital Forensics Investigation
The process of digital forensics typically involves the following steps:
- Identifying the Source of Evidence: This step involves locating the digital devices or networks that may contain useful evidence.
- Acquiring Digital Evidence Without Tampering: Experts use specialized tools to gather data while ensuring its integrity is maintained.
- Analyzing and Interpreting Data: Investigators examine the evidence to identify useful information, whether it’s about the attack method or lost files.
- Reporting Findings: Findings are documented thoroughly, ensuring the evidence can be used in a legal or investigative context.
Common Causes of Data Loss

Data loss is more common than we think, and it can occur for various reasons:
- Human Error: Accidental deletion, overwriting files, or incorrect file handling are common causes.
- Hardware Failures: Disk damage, corrupted drives, or malfunctioning hardware can make data inaccessible.
- Malware and Cyber Attacks: Cybercriminals can delete, encrypt, or corrupt your files in a ransomware attack or malware infection.
- Natural Disasters and Unforeseen Events: Fires, floods, or power outages can cause physical damage to storage devices.
Methods to Recover Lost Data
Basic Techniques
If you find yourself facing data loss, the first step is often to check the following:
- Recycle Bin or Trash: You’d be surprised at how often files can be restored from the Recycle Bin or Trash, often without needing specialized tools.
- Built-in OS Recovery Tools: Both Windows and macOS offer recovery tools that can help you restore lost files.
Advanced Tools and Software
For more complex data loss situations, advanced recovery tools can help:
- Third-Party Recovery Applications: Software like Recuva or Stellar Data Recovery specialize in scanning your drive for recoverable data. These tools can retrieve files that may have been deleted or corrupted.
- Features to Look for in Data Recovery Tools:
- Easy-to-use interface
- Ability to scan various file types
- Support for damaged or formatted drives
- Features to Look for in Data Recovery Tools:
Professional Data Recovery Services
If your data loss is caused by physical damage or encryption from a cyberattack, professional help may be necessary. At C9Lab, experienced professionals use cutting-edge techniques and forensic tools to recover data from a variety of devices, ensuring no detail is overlooked. C9Lab’s data recovery services cover all branches of digital forensics, from recovering data on damaged hardware to retrieving deleted or hidden information from mobile devices and cloud storage.
- When to Seek Professional Help: If the data is critical, or if you’ve tried basic recovery methods without success, reaching out to data recovery experts is your best option.
- Benefits of Expert Intervention: Professionals can recover data from damaged devices, retrieve encrypted data, or perform deep analysis to restore files in complex situations.
Tools and Techniques Used in Digital Forensics
| Forensic Analysis Tools | Network Forensics Tools | Mobile Forensics Tools | Data Recovery Tools | Password Cracking Tools |
| FTK (Forensic Toolkit) | X1 Social Discovery | Oxygen Forensic Detective | Disk Drill | Passware |
| EnCase | Kali Linux | Magnet AXIOM | Recuva | |
| Autopsy | Wireshark | Cellebrite UFED | ||
| ProDiscover | ||||
| OSForensics |
Digital forensics relies heavily on specialized tools and techniques to recover, analyze, and preserve data. Some of the most commonly used tools and methods in the field include:
1. Data Imaging Tools
- FTK Imager: A tool used to create bit-for-bit copies of data from hard drives, USB devices, and other media without altering the original evidence. This is critical for preserving evidence.
- EnCase: Widely used in law enforcement, EnCase is an all-in-one digital forensics tool that enables investigators to capture, analyze, and preserve data.
2. File Recovery and Analysis Tools
- Autopsy: An open-source digital forensics platform for investigating hard drives and smartphones. It helps analyze file systems, search for deleted files, and recover hidden data.
- X1 Social Discovery: This tool specializes in collecting and analyzing social media and other online communications, which is crucial for cybercrime investigations.
3. Malware Analysis Tools
- Cuckoo Sandbox: A tool used for automating the analysis of malware. It provides a detailed report on how malware behaves within a controlled environment.
- Wireshark: An open-source network protocol analyzer that allows for deep inspection of network traffic, useful in tracing malicious data transfers or identifying cybersecurity incidents.
4. Data Recovery Tools
- R-Studio: A powerful tool used to recover data from damaged or formatted storage devices. It works with numerous file systems and provides a user-friendly interface.
- Ontrack Data Recovery: A leading tool for recovering lost data due to logical and physical failures. It is often used by professionals to recover data from damaged hard drives or RAID systems.
5. Data Preservation Techniques
- Write Blockers: Devices or software tools used to prevent writing to a storage device during the forensic process. Write blockers ensure that data is not altered during the acquisition phase, maintaining the integrity of evidence.
- Bit-For-Bit Imaging: This technique captures an exact replica of the storage device, ensuring that every bit of data, including deleted files and hidden partitions, is preserved.
Preventing Future Data Loss
Regular Backups: Cloud and Physical Options
To avoid the stress of data loss, setting up a reliable backup strategy is crucial. Consider:
- Cloud Backups: Services like Google Drive or Dropbox offer convenient, automatic backups.
- Physical Backups: External hard drives and RAID systems provide physical backups that you can store off-site for added security.
Implementing Robust Security Measures Against Cyber Threats
- Firewalls and antivirus software protect your devices from external threats.
- Regular security patches and software updates help prevent malware and cyberattacks from causing data loss.
Educating Users on Safe Data Handling Practices
Employees and individuals should be trained on the importance of secure data handling practices. Encourage:
- Strong, unique passwords
- Avoiding suspicious email links or attachments
- Encrypting sensitive files
Using Reliable Hardware and Software
Investing in high-quality storage devices and using trusted data recovery software can prevent the risk of data loss.
Conclusion: Digital Forensics and Data Recovery Essentials
In today’s digital landscape, digital forensics is more important than ever in helping us understand and recover from data loss incidents. Whether you’re an individual trying to recover lost memories or a business protecting sensitive data, the process of digital forensics can be a powerful tool for investigation and recovery.

Encouraging Proactive Measures
While it’s comforting to know that data recovery is possible, prevention is always better than recovery. Make sure to back up your data regularly, implement solid security measures, and educate yourself on how to handle your data safely. If you’re dealing with complex data loss issues, don’t hesitate to consult professionals. They can help you recover your data efficiently and ensure that it’s protected from future threats.
Take control of your data security today—because your data deserves protection.
FAQs
1. What is Digital Forensics?
Digital forensics is the process of identifying, preserving, analyzing, and presenting digital evidence from electronic devices like computers, smartphones, and networks. It’s crucial for investigating cybercrimes, data breaches, and other digital incidents.
2. What is Digital Forensics in Cybersecurity?
In cybersecurity, digital forensics helps investigate and resolve security breaches or cyberattacks. By analyzing digital evidence, forensic experts can trace malicious activities, identify vulnerabilities, and improve security measures to prevent future threats.
3. What is the Digital Forensics Life Cycle?
The digital forensics life cycle involves several steps:
- Identification: Recognizing potential evidence sources.
- Collection: Safely gathering data without altering it.
- Examination: Analyzing the collected data for relevant information.
- Analysis: Interpreting the data to draw meaningful conclusions.
- Presentation: Documenting findings and presenting them in a legal context, if necessary.
4. What are the Types of Digital Forensics?
Digital forensics encompasses various subfields, including:
- Computer Forensics: Recovering data from computers and storage devices.
- Network Forensics: Analyzing network traffic for signs of unauthorized access.
- Mobile Forensics: Recovering data from mobile devices like smartphones.
- Cloud Forensics: Investigating data stored in cloud services.
- Database Forensics: Recovering data from databases to uncover potential misuse.
5. What are Digital Forensics Tools?
Digital forensics tools are specialized software used to analyze and recover digital evidence. Popular tools include:
- EnCase: Forensic analysis and evidence collection.
- FTK (Forensic Toolkit): Data analysis with indexing features.
- Autopsy: An open-source tool for hard drive analysis.
- Wireshark: A network protocol analyzer for monitoring network traffic.
Follow us on LinkedIn and Subscribe to our newsletter 📩 for the latest cyber security updates, insightful articles, and exclusive content to help you navigate the ever-changing threat landscape.
Don’t forget to check out our Website 🌐 to make your cyberspace safe and secure 🔒, and join our growing community on Instagram 📸 for bite-sized cyber security tips and trends. 💻 🔍


