
What is Quantum Computing? Why it is a Threat to Cyber Security
Table of Contents
Remember the Y2K bug panic? The world held its breath as the year 2000 approached, fearing that computers wouldn’t be able to handle the date change and critical systems would crash. While the damage was minimal in the end, that collective anxiety was a taste of what we might face with the looming quantum computing revolution. But this time, the stakes are even higher. Quantum computing, a mind-boggling technology once confined to science fiction, is rapidly becoming a reality. And while it promises incredible advancements, it’s also a ticking time bomb for our current cybersecurity infrastructure.
What Is Quantum Computing?
Quantum computing is an exciting and rapidly developing field that utilizes the principles of quantum mechanics to perform computations. Unlike classical computers, which use bits (0s or 1s), quantum computers use qubits. These quirky quantum bits can exist in multiple states simultaneously, thanks to a mind-bending concept called superposition. This, combined with entanglement (a sort of quantum telepathy), gives quantum computers their immense power.
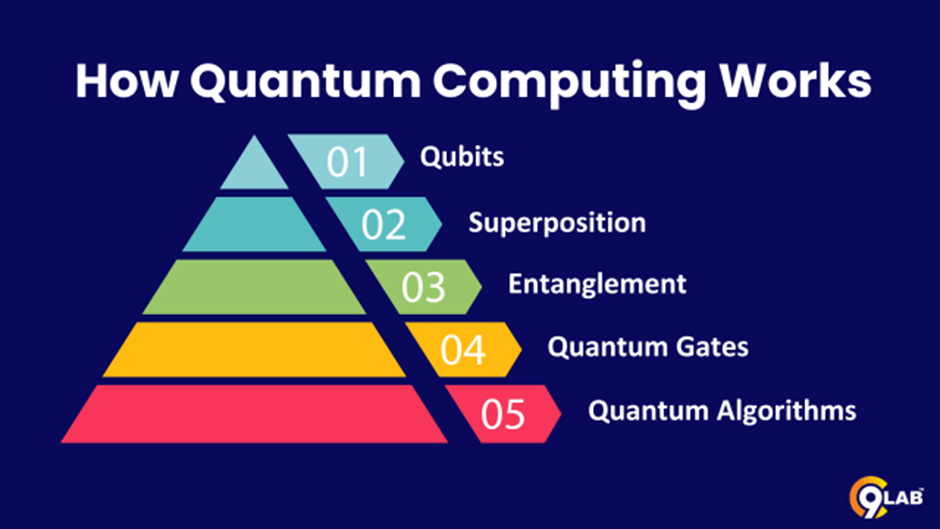
There are several key aspects to quantum computing:
- Qubits – In classical computing, the fundamental unit of information is a “bit.” It’s like a switch that can be either on (1) or off (0). Quantum computing uses “qubits” instead. These are not limited to just two states. A qubit can exist in a superposition, a blend of 0 and 1 simultaneously. Imagine a coin spinning in the air—it’s neither heads nor tails until it lands. Similarly, a qubit holds the potential for both 0 and 1 until measured. This ability to exist in multiple states at once is what gives quantum computers their extraordinary power.
- Superposition – Superposition allows a quantum computer to explore multiple possibilities at the same time. It’s like being able to try all the possible routes through a maze simultaneously, rather than trying them one by one. This parallel processing capability is what makes quantum computers potentially exponentially faster than classical computers for certain types of problems.
- Entanglement – Entanglement is a fascinating phenomenon where two or more qubits become interconnected, regardless of the distance between them. When qubits are entangled, the state of one qubit instantly affects the state of the other, even if they are miles apart. This seemingly magical connection is a key resource in quantum computing, allowing for intricate and powerful computations.
- Quantum Gates – In traditional computers, logic gates (like AND, OR, NOT) are used to manipulate bits and perform calculations. Quantum gates serve a similar purpose, but they manipulate qubits instead. These gates utilize the principles of superposition and entanglement to orchestrate intricate sequences of operations, unlocking the full potential of quantum computing.
- Quantum Algorithms- Just as traditional computers rely on algorithms to solve problems, quantum computers also use algorithms, but they are tailored to leverage the unique properties of qubits and quantum gates. These specialized algorithms are designed to solve specific problems that classical computers struggle with, such as factoring large numbers (crucial for cryptography) or simulating complex molecular interactions (important for drug discovery).
Why Quantum Computing is a Big Deal
Quantum technology isn’t just about faster computers; it’s about fundamentally changing how we solve problems. Here’s why quantum computing is making waves across industries:
- Drug Discovery: Quantum computers could simulate the complex interactions of molecules, accelerating the development of new drugs and treatments.
- Materials Science: Designing new materials with unprecedented properties could revolutionize manufacturing and transportation.
- Financial Modeling: Quantum algorithms could optimize investment portfolios and assess risk more accurately.
- Artificial Intelligence: Quantum machine learning could lead to breakthroughs in areas like natural language processing and image recognition.
- Climate Modeling: By simulating complex climate systems, quantum computers could help us better understand and address climate change.

Quantum Attacks: A Cybersecurity Nightmare
Quantum computing poses a significant threat to cybersecurity primarily because of its potential to break widely used encryption algorithms that secure sensitive data and communications.
Here’s how:
- Breaking Public-Key Cryptography: Most current encryption schemes, such as RSA and ECC, rely on the difficulty of factoring large numbers or solving discrete logarithm problems. These problems are computationally infeasible for classical computers, making the encryption secure. However, quantum computers equipped with Shor’s algorithm could solve these problems efficiently, rendering these encryption methods obsolete.
- Quantum Harvest Threatens Encrypted Data: Even if large-scale quantum computers aren’t available yet, malicious actors can still pose a threat. They can intercept and store encrypted data now, with the expectation of decrypting it later when powerful quantum computers become available. This means that even data considered secure today could be vulnerable in the future.
- Impact of Quantum mechanics on Critical Infrastructure: Many critical systems, like banking, healthcare, and government infrastructure, rely on encryption for security. If quantum computers break these encryption schemes, it could lead to large-scale data breaches, financial losses, identity theft, and even disruptions to essential services.
- Developing Quantum-Resistant Cryptography: Researchers are actively working on developing new encryption algorithms that are resistant to quantum attacks. These “post-quantum cryptography” methods aim to ensure the security of data and communications in the era of quantum computing. However, the transition to these new methods will take time and resources.
In conclusion, while quantum computing offers immense potential for various fields, its ability to break current encryption methods poses a significant threat to cybersecurity. The development of quantum-resistant cryptography and the transition to new security protocols are crucial for safeguarding sensitive data and communications in the future.
What’s at Stake?
- Mass Data Breaches: Your personal information, financial data, and company secrets exposed on a massive scale.
- Critical Infrastructure Attacks: Power grids, transportation systems, and financial markets disrupted or even shut down.
- Economic Chaos: The global economy thrown into turmoil as trust in digital systems erodes.
Don’t Wait Until It’s Too Late
Contact us today for a free consultation to discuss your cybersecurity needs. Let us help you fortify your digital defenses before the quantum storm hits. The future of your data security starts now.
FAQ
1. What is quantum computing?
Quantum computing uses qubits, which can exist in multiple states simultaneously, offering much greater computing power compared to classical bits.
2. How is quantum computing different from classical computing?
Classical computing uses bits (0s and 1s), while quantum computing uses qubits that can represent both 0 and 1 at the same time.
3. Why is quantum computing powerful?
It’s power comes from superposition (qubits in multiple states) and entanglement (interconnected qubits affecting each other instantly).
4. Why is quantum computing a cybersecurity threat?
Quantum computers can break current encryption methods like RSA and ECC, making sensitive data vulnerable.
5. What is quantum-resistant cryptography?
It’s encryption designed to withstand quantum attacks, protecting data from future quantum computers.
6. How could quantum computing impact critical systems?
Quantum attacks could break encryption, leading to data breaches, financial loss, and disruption of essential services.
Ready to secure your business in the quantum age? Click here to talk to our experts or explore our quantum-safe solutions




